Dark Web Monitoring to Stop Leaks Before They Happen
In the ever-evolving landscape of cybersecurity threats, preventing data breaches has become a top priority for organizations worldwide. As technology advances, so do the methods employed by cybercriminals to compromise sensitive information. One proactive approach gaining prominence in the fight against cyber threats is Dark Web monitoring. By leveraging the capabilities of Dark Web monitoring, businesses can identify potential threats before they escalate into full-fledged data breaches.
Understanding the Dark Web Monitoring
The Dark Web, a hidden part of the internet not indexed by traditional search engines, serves as a breeding ground for illicit activities. It is a haven for cybercriminals who buy, sell, and exchange stolen data, hacking tools, and other illegal services. To fortify their cybersecurity defenses, organizations are turning to Dark Web monitoring to detect early signs of potential threats and vulnerabilities.
The Role of Dark Web Monitoring
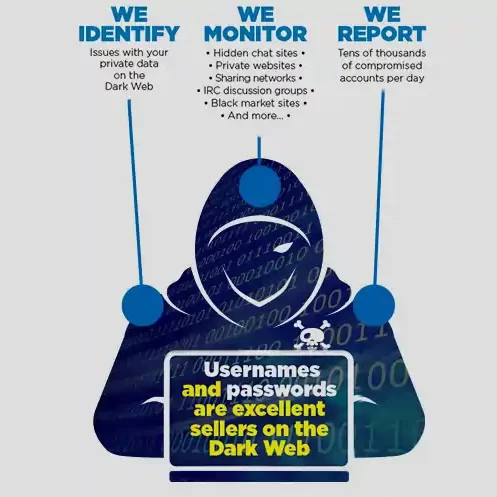
Dark Web monitoring involves tracking online platforms on the Dark Web where cybercriminals operate. This includes forums, marketplaces, and chat rooms where stolen data is bought and sold. By continuously monitoring these channels, cybersecurity professionals can identify compromised credentials, leaked sensitive information, and discussions related to potential attacks.
One of the primary benefits of Dark Web monitoring is the ability to proactively address vulnerabilities before they are exploited. Rather than reacting to a data breach after the fact, organizations can take preventive measures to secure their systems and protect sensitive information.
Early Detection of Compromised Credentials
One common method employed by cybercriminals is the use of compromised credentials to gain unauthorized access to organizational systems. Dark Web monitoring tools actively search for credentials that may have been exposed in data breaches. By identifying compromised usernames and passwords early on, organizations can take swift action, such as enforcing password resets and implementing multi-factor authentication, to prevent unauthorized access.
Protection Against Insider Threats
Insider threats pose a significant risk to organizations, as employees with malicious intent or unintentional negligence can compromise sensitive data. Dark Web monitoring allows organizations to detect signs of insider threats by monitoring for unusual activities or the sale of internal information on the Dark Web. This early detection enables organizations to investigate and address potential insider threats before they escalate.
Proactive Vulnerability Management
Cybercriminals often exploit vulnerabilities in software, networks, or applications to gain unauthorized access. Dark Web monitoring can be a crucial component of proactive vulnerability management by identifying discussions or activities related to potential exploits. This information allows organizations to patch vulnerabilities promptly, minimizing the risk of a successful cyber attack.
Strategic Threat Intelligence
Dark Web monitoring provides valuable threat intelligence that can inform an organization’s cybersecurity strategy. By understanding the tactics, techniques, and procedures employed by cybercriminals, organizations can better prepare for potential attacks. This intelligence can be used to enhance security controls, update policies, and educate employees on emerging threats.
Enhancing Incident Response
In the event of a security incident, rapid response is crucial to mitigate the impact and prevent further damage. Dark Web monitoring contributes to a more effective incident response by providing early indicators of a potential breach. Security teams can use this information to trace the origin of the threat, identify affected systems, and take swift action to contain and eradicate the threat.
Challenges and Considerations
While Dark Web monitoring offers significant advantages in preventative cybersecurity, there are challenges and considerations that organizations must address. Privacy concerns, legal implications, and the dynamic nature of the Dark Web present complexities that require careful navigation. Additionally, organizations need to invest in skilled cybersecurity professionals and robust monitoring tools to effectively leverage Dark Web monitoring as part of their cybersecurity strategy.
Conclusion
In the ongoing battle against cyber threats, preventative measures are essential to safeguard sensitive information and maintain the trust of customers and stakeholders. Dark Web monitoring has emerged as a valuable tool in the cybersecurity arsenal, allowing organizations to detect and address potential threats before they escalate into damaging data breaches. By proactively monitoring the Dark Web, organizations can stay one step ahead of cybercriminals, fortifying their defenses and ensuring the security of their digital assets. As the cyber threat landscape continues to evolve, embracing preventative cybersecurity measures like Dark Web monitoring will be a critical component of a robust and resilient security posture.